You have chosen a
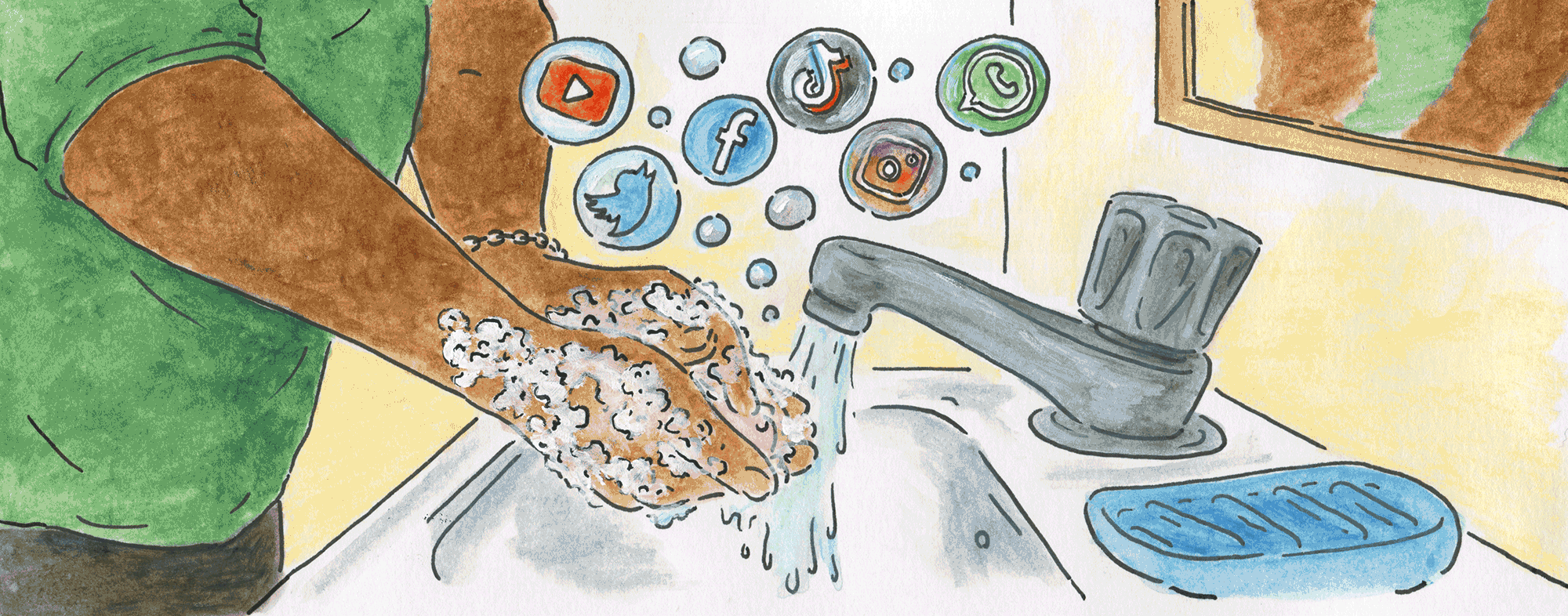
A fundamental food safety practice is to sanitize our hands, which within social networks and e-mails is equivalent to security and privacy settings, because they are an important layer before producing and tasting everything.
For a hygiene that really protects you, don’t forget to go through all the configuration steps. Think carefully about what information about you is available to everyone.
* For this step you need to be logged in, that is, be logged into your accounts.
The use of strong passwords is the first change we must make in our dietary re-education, oops… In our digital re-education! It is the rice of Brazilians.
When creating your password, do not use personal information and/or data that can be easily found on the Internet, in leaked data or in our social networks, no birthday dates (yours or anyone else’s), no name of mother, grandmother, pet or favorite club, single words and sequences of numbers are very easy to be broken into, and never use the same password (or with small variations) for more than one service or login.
But don’t panic buddy, below you will know everything to change them for stronger passwords!
“But how to create strong passwords?” KFB, 61.
Long sentences with spaces make great passwords! And we can increase the complexity by mixing in slang, idioms, and words from different cultures. To keep your passwords strong, get into the habit of changing them often or whenever you learn that you have had a leak from a service you use. Check here if you have had any leaks associated with your emails: https://monitor.firefox.com
“Help! It’s too many passwords, I don’t know what to do!” LGM, age 42.
Easy girl, digital life requires creating passwords for almost everything, but it also brought us an excellent solution, the “password managers” which are apps/programs/softwares, that help us save and organize all our passwords, in one place, and even create random passwords <3. We recommend KeepassXC, learn more in the
get hands-on section.
So, what not to do?
– Passwords are personal, so don’t share your password with anyone. not even to a trusted date, not even to a super friend! NOT ANYONE!
– Don’t abandon old accounts and e-mails. Remember to delete the old services so that you won’t be surprised in the future!
– Don’t save passwords in your browser! If your cell phone is not encrypted, in case of theft, robbery or confiscation, remember that they will have access to ALL your services, ALL of them!
Let’s “get hands-on” and increase the strength of your passwords? Download KeepassXC and learn how to use it here!
Did you think you were done? We have one more little thing to add, and it is called beans! Rice should always go with beans, here in this case that ingredient is the two-step verification, ever heard of it?
Because of the amount of theft/kidnapping of social networks, messengers, accounts and e-mail (with the intention of financial scams or online harassment), an extra security mechanism was created for these accounts, to prevent someone from impersonating you. So besides the password, which is something you (or your password manager) should know, the two-step 2-factor verification associates your account with something you must have, i.e. it asks for a code that you receive through SMS, e-mail, or a cell phone app linked to the account. Enable this function on all accounts and services that you can. Do it now and avoid headaches!
Curiosity: Every year a world ranking is made of the most used (and most leaked) passwords, if any of your passwords is the same as one of these, you better change it now! Friend warning. 😉
The “vigor” of our digital re-education is going to be safe browsing! Many people browse the Internet every day, with more or less time dedicated to this task.
But this task can bring security breaches and harm our free and happy online existence. But with some care, attention and the help of some extensions to these browsers we can make this care much simpler.

When we think of organic food it soon comes to mind, aaaaaahhhhhh, but it is very expensive! Yes, buying it at the supermarket is expensive, but just as there are organic food at more affordable prices, there are many ways to migrate and use free software…
The first comparison we make is in relation to the difference between the unreal facilities of the supermarket versus the temporalities and family farming of organics. That is, it is not real and sustainable to buy strawberries all year round, fruits and vegetables have seasons to be produced and if you want to eat everything all the time, you will eat a lot of agrotoxics! In the same way free software is cultivated by a community of activists and developers in a collaborative and non-profit way, so it is not fair to compare it to the same logic of productivity as proprietary software (in the case of organic, the supermarket!).
This doesn’t mean that they are worse or more difficult, it means that when you commit to use them you need to take into consideration that you are breaking the client and service logic and entering a project where the community speaks louder, just like with organic food. But let’s get to the ABC of free software:
What is Free Software? There are 4 freedoms that make a piece of free software:
Salads are very important for the proper functioning of the body, they bring us vitamins, proteins and minerals that are fundamental for our immune system. Here we will deal with secure e-mails with the same function, to protect us and the services we register with.
“Free” services make their profit by selling the data we provide when using the service to third parties. In this case, we and our wishes, are the product.
Using e-mail services that are transparent about the use of our data, that respect our privacy, and that traffic the information scrambled (encrypted) over the networks, is a small big step. We know it’s not easy to change the convenience of a Google account that already easily logs into everything, but this has consequences, if you don’t want to have your affections and desires captured by large companies that only aim to increase profits, consider migrating to one of the services below:
They are there all the time tempting us, taking our attention away, but everybody likes them, everybody wants them, and just like a piece of cake, it’s hard to hold back after the first bite, oops… message! But with knowledge we can decide for healthier desserts or for messier ones!

Churros are fried, full of saturated fat, not very healthy, and if you eat too many, they can cause heartburn. Churros is the Whatsapp of our menu. Developed under the logic of profiting from our data, it can share information from your account and how you use the service with other Facebook companies, including for advertising. Moreover, it does not encrypt our messages when we back up to the cloud. But it is the app that everyone has, and sometimes it is even free. Nice, right? But look at the cholesterol. So if it’s hard not to fall into temptation, at least try to eat in moderation!
Bread pudding. This famous trick to use stale bread is like Telegram’s encryption, so, kind of tricky. It is not enabled by default, only in secret chats, the ones we open with the little lock, which are also the only way to use message self-destruction. But neither encryption nor self-destruction is available in groups, which are exposed to leaks. Even Telegram’s free software is half-assed, only half-free. But who doesn’t like the variety of stickers, gifs and bots that are available there? And, among all of them, it is the only one that lets us communicate without exposing our phone number. Who can resist Grandma’s bread pudding?

Pumpkin pudding is more elaborate than pudding. The process is manual, from peeling the pumpkin to stirring the pan for some time. This is Signal, free software, developed in community, which has privacy and security as its main value. The encryption is guaranteed in every type of chat, you can enable the little self-destruct clock in any type of chat, but there is no telephone number secrecy.
These are services made and provided by a community of people concerned with building a free internet, and are intended for people, communities and organizations that propose to create a fair and oppression-free society, all these services have a maintenance cost, always contribute to the community of the services you use, either with money or by volunteering.

Salt File sharing Share Riseup
Limited to 50 MB files. Files available for up to 12h. Parsley
Videoconferencing Jitsi
Chimamanda (Vedetas) and Jit.si
Parsley
Videoconferencing Jitsi
Chimamanda (Vedetas) and Jit.si  Coriander
Videoconferencing BigBlueButton
Angela (Vedetas) and BigBlueButton (trial version only)
Coriander
Videoconferencing BigBlueButton
Angela (Vedetas) and BigBlueButton (trial version only)  Pepper
PAD or collaboratively edited notepad
Antonieta (Vedetas)
Riseup
Board, it allows you to place images.
Pepper
PAD or collaboratively edited notepad
Antonieta (Vedetas)
Riseup
Board, it allows you to place images.  Rosemary
spreadsheet with collaborative editing.
Ethercalc and Eveliyn (Vedetas)
Rosemary
spreadsheet with collaborative editing.
Ethercalc and Eveliyn (Vedetas)
 Cumin
VPN (Virtual Private Network) – virtual private network, makes it possible to connect to a service without revealing your real IP
Riseup VPN
Cumin
VPN (Virtual Private Network) – virtual private network, makes it possible to connect to a service without revealing your real IP
Riseup VPN  Sweet Paprika
Metadata cleanup
Systemli
Files up to 128MB.
Sweet Paprika
Metadata cleanup
Systemli
Files up to 128MB.  Hot Paprika
Secure file storage
Nextcloud (Systemli) and Mega
Hot Paprika
Secure file storage
Nextcloud (Systemli) and Mega 
Get into the habit of deleting photos, videos, messages and audios, and if you need to keep something, opt for safer places like encrypted clouds (Mega and Nextcloud), instead of carrying everything around.
Learn how to clean up data on Android.
When we want to have a spare of a wonderful food that we are eating we can make one lunchbox and save it to enjoy the same flavor again. It may not be the perfect analogy, but when it comes to our data we can have a backup.
This little word has been keeping us awake at night since we began to delegate the processing and storage of our important information to the computer. These are contacts, communications, e-mails, documents, photos, music, in other words, an infinite amount of data. But it’s always possible for a “problem” to occur along the way. Our computer, cell phone, hard drive, cloud or pen drive can malfunction, be stolen, taken by authorities, or we can even fall victim to an attack and lose access to online content or even access to the files on our devices.
Cuidados com Phishing

Phishing is a cybercrime technique where someone pretends to be an acquaintance to manipulate people into obtaining confidential information.
Do you know when you are being phished? Go to https://phishingquiz.withgoogle.com/?hl=es-419 and find out.
virus, malware, ransomware…
Our food can contain poison (pesticides) that are imperceptible to the naked eye, also our surfing and communicating on the internet can bring us risks that at first sight are also invisible! Just as in real life, the Internet is not free from malicious people and scammers. We need to be aware and present in our online actions, so that we do not become victims.
And knowledge is the key! But what is virus? And how do they attack?
A virus or malware is a “malicious software” used to cause harm to computer or cell phone users. It is able to act in a very broad way, which includes:


Many people can’t eat in peace if they don’t post something and check-in on their networks! But do we need to show everyone besides what we like to eat, where we are, all the time?
Using the check-in tool on social networks can make people already exposed vulnerable and make threats that are in the digital world become physical too, after all, you will be giving your location on a platter to anyone who has access to your profile!
Also, once you leave your location on for your cell phone’s operating system, Google or Apple, it turns our phones into a pocket tracker, leaving a trail of where we have been all the time! That’s why it’s always best to leave your location settings off, both those on your phone, and those on apps like Facebook, Twitter, and Instagram!
More information:
Location Tracking
Pause your Google account’s location history